When dealing with compressed files, especially encrypted ones, cracking passwords becomes an essential skill. Hashcat is a powerful password cracking tool that supports a variety of encryption algorithms and greatly enhances cracking efficiency through GPU acceleration. In this article, we will discuss how to use Hashcat to crack passwords for different types of compressed files, including ZIP, RAR, and 7z files, and provide detailed instructions on selecting the appropriate hash mode.
1. Introduction to Hashcat
Hashcat is an open-source password cracking tool that supports both CPU and GPU acceleration for password recovery. With its powerful attack modes (such as dictionary attack, brute force, rule-based attacks, etc.), Hashcat can crack many encryption protocols, hash algorithms, and password-protected compressed files. To crack the passwords of compressed files, Hashcat requires extracting the hash value from the files and then launching an attack based on these hash values.
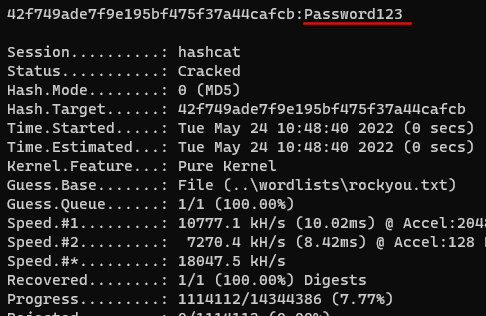
2. Preparations
Before using Hashcat to crack compressed file passwords, you need to complete the following preparations:
- Install Hashcat: You can download and install the version of Hashcat suitable for your operating system from the Hashcat official website.
- Prepare Compressed Files: Ensure you have the compressed files (such as ZIP, RAR, 7z, etc.) that you need to crack.
- Prepare a Dictionary File: Dictionary attacks are the most common cracking method; using a strong dictionary (such as
rockyou.txt) can significantly increase your success rate. - Ensure GPU Support: Hashcat utilizes GPU for acceleration, which can dramatically improve cracking speed. Be sure that your system has the appropriate graphics driver installed (like NVIDIA CUDA or AMD OpenCL).
3. Extracting Hash Values from Compressed Files
Hashcat cannot directly crack the compressed files themselves; it cracks the hash values extracted from them. We will need to use some tools to extract these hash values from the compressed files before using Hashcat for password cracking.
1. Cracking ZIP Passwords
For ZIP files, we can use the zip2john tool (which is included with John the Ripper) to extract the hash value. Assuming your ZIP file is called file.zip, you can execute the following command:
|
|
This will generate a zip_hash.txt file containing the hash value of the ZIP file.
2. Cracking RAR Passwords
For RAR files, the rar2john tool is used to extract the password hash. Assuming your RAR file is named file.rar, execute the following command:
|
|
This will create a rar_hash.txt file containing the RAR file’s hash value.
3. Cracking 7z Passwords
The hash values from 7z files can be extracted using a similar approach with the 7z2john tool:
|
|
This will extract the hash value of the 7z file and save it to 7z_hash.txt.
4. Choosing the Right Hash Mode
Hashcat needs to know the encryption type of the file in order to select the correct cracking algorithm. Different compressed formats and versions (like ZIP, RAR, etc.) use different hash modes. Below are the common compressed file formats and their corresponding hash modes.
1. ZIP Files
ZIP files have multiple versions of encryption, with common types including traditional ZIP encryption and AES encryption.
-
ZIP Files (Traditional ZIP Encryption, ZIP2):
- Hash Mode:
-m 13600 - Used for the classic ZIP encryption format, supporting older versions of ZIP files.
Example command:
1hashcat -m 13600 zip_hash.txt rockyou.txt - Hash Mode:
-
ZIP Files (AES Encryption):
- Hash Mode:
-m 13400 - Used for AES-encrypted ZIP files, which are typically the newer ZIP file format.
Example command:
1hashcat -m 13400 zip_hash.txt rockyou.txt - Hash Mode:
2. RAR Files
RAR files have two main versions, RAR3 and RAR5, which utilize different encryption algorithms and require different hash modes.
-
RAR3 Files (Old Version RAR Files):
- Hash Mode:
-m 12500 - Used for RAR3 format files, employing older encryption algorithms.
Example command:
1hashcat -m 12500 rar_hash.txt rockyou.txt - Hash Mode:
-
RAR5 Files (New Version RAR Files):
- Hash Mode:
-m 13000 - Used for RAR5 format files, supporting stronger encryption algorithms.
Example command:
1hashcat -m 13000 rar_hash.txt rockyou.txt - Hash Mode:
3. 7z Files
7z files support AES encryption, and Hashcat uses the following hash mode for cracking:
-
7z Files (AES Encryption):
- Hash Mode:
-m 11600 - Used for classic 7z file encryption (including AES encryption).
Example command:
1hashcat -m 11600 7z_hash.txt rockyou.txt - Hash Mode:
4. Summary of Hash Mode Selection
| Compressed Format | Hash Mode | Description |
|---|---|---|
| ZIP | -m 13600 |
Classic ZIP encryption format |
| ZIP | -m 13400 |
AES-encrypted ZIP files |
| RAR | -m 12500 |
RAR3 files (old version RAR files) |
| RAR | -m 13000 |
RAR5 files (new version RAR files) |
| 7z | -m 11600 |
AES-encrypted 7z files |
5. Starting the Cracking Process
Once you have selected the appropriate hash mode, you can begin cracking the compressed file passwords using Hashcat. There are two common attack methods to use:
1. Dictionary Attack
A dictionary attack is the most typical method. Hashcat will attempt every password from the dictionary until it finds a match. If we use rockyou.txt as the dictionary file, you can run the following command:
|
|
For RAR files, the command would be:
|
|
2. Brute Force Attack
If the dictionary attack is unsuccessful, a brute force attack is an alternative option. A brute force attack will try every possible password combination. Here is an example command for brute force:
|
|
In this command, ?a denotes all character sets, including letters, numbers, and symbols. You can adjust the password length as needed.
6. Conclusion
The process of using Hashcat to crack compressed file passwords involves extracting hash values, selecting the appropriate hash mode, and choosing the right attack method (such as a dictionary or brute-force attack). Selecting the correct hash mode is crucial for successful password recovery, as different compressed formats and versions correspond to different hash modes. By properly configuring parameters and utilizing GPU acceleration along with a robust dictionary file, you will be able to efficiently crack compressed file passwords.
